Sealed Records Exposed In Major Court Gaffe
Prosecutors scramble to cloak ongoing probe details
APRIL 22--In a shocking failure to protect sensitive details about dozens of ongoing criminal investigations, federal officials somehow allowed confidential information about sealed cases to be publicly accessible via the court system’s online lookup service, The Smoking Gun has learned.
Over the past nine months, details of 40 separate sealed court applications filed by federal prosecutors in Alabama were uploaded to PACER, the web-based records system that counts nearly one million users, including defense lawyers, prosecutors, journalists, researchers, private investigators, and government officials.
 The court applications, made by ten separate prosecutors, included requests to install hidden surveillance cameras, examine Facebook records, obtain credit information on certain individuals, procure telephone records, and attach devices on phone lines that would allow agents to track incoming and outgoing calls. Remarkably, the U.S. District Court records--which covered filings as recent as April 11--included specific names, addresses, and phone numbers that should never have appeared on PACER.
The court applications, made by ten separate prosecutors, included requests to install hidden surveillance cameras, examine Facebook records, obtain credit information on certain individuals, procure telephone records, and attach devices on phone lines that would allow agents to track incoming and outgoing calls. Remarkably, the U.S. District Court records--which covered filings as recent as April 11--included specific names, addresses, and phone numbers that should never have appeared on PACER.
The confidentiality breach was first discovered by a TSG reporter and brought to the attention of Department of Justice representatives and court officials in the Middle District of Alabama, which is comprised of 23 counties and includes Montgomery, the state’s second-largest city. By late yesterday afternoon, prosecutors had the confidential information scrubbed from the online records system and placed under judicial seal at the federal courthouse in Montgomery (pictured above).
It is likely impossible to determine if the sensitive information was viewed or disseminated by other PACER users, let alone gauge whether any cases were jeopardized by the posting of the sealed material.
Prosecutors were incredulous when told that law enforcement sensitive information was available on PACER. A Justice Department source termed it a “disastrous situation” for which prosecutors were not responsible. One government lawyer said they were “shocked” to discover that details from sealed court applications were essentially sitting in plain sight.
 While Debra Hackett, the U.S. District Court clerk, initially told TSG that federal prosecutors were to blame for failing to have certain information properly sealed, her position apparently shifted after discussions with United States Attorney Leura Canary (seen at left). Canary, a source said, was “appalled” to discover that court employees had made the confidential information publicly available.
While Debra Hackett, the U.S. District Court clerk, initially told TSG that federal prosecutors were to blame for failing to have certain information properly sealed, her position apparently shifted after discussions with United States Attorney Leura Canary (seen at left). Canary, a source said, was “appalled” to discover that court employees had made the confidential information publicly available.
In a statement provided late yesterday to TSG, the Middle District’s chief judge, Mark Fuller, noted that, “The confidential information has been sealed. I regret the error was not identified earlier and have adopted procedures to ensure that it will not occur in the future.” It remains unclear why U.S. District Court personnel believed that, while the documents themselves had to be kept in a safe in the clerk’s office, details from those records could be made available through PACER.
The bulk of the 40 court applications involved prosecutors seeking judicial authorization to obtain telephone records and/or the placement of pen registers and trap and trace devices on targeted phones. A pen register tracks outgoing phone numbers, while a trap and trace captures incoming numbers.
The use of the devices is a standard investigative technique employed by federal agents handling narcotics, organized crime, public corruption, and fugitive cases. Information gathered by the devices can provide investigators with a nexus between suspects, help identify additional targets, and aid in the establishment of the probable cause needed to wiretap phone calls.
While the physical court applications themselves were successfully sealed--as were the related orders signed by federal judges--and not available to be downloaded in PDF form from PACER, the online entries for these cases (known as “criminal miscellaneous” files) included the confidential information.
For example, 35 sealed applications dealt with a total of 39 separate phone numbers being targeted by federal investigators. In each instance, the phone number was actually included in the PACER entry. As a result, TSG reporters were able to use public databases and online searches to identify several individuals whose phone usage is of interest to criminal investigators. Some of the targeted numbers included area codes for cities like Miami, Houston, Chicago, Atlanta, and Los Angeles.
The names of five individuals for whom prosecutors sought court permission to obtain credit information were also uploaded to PACER.
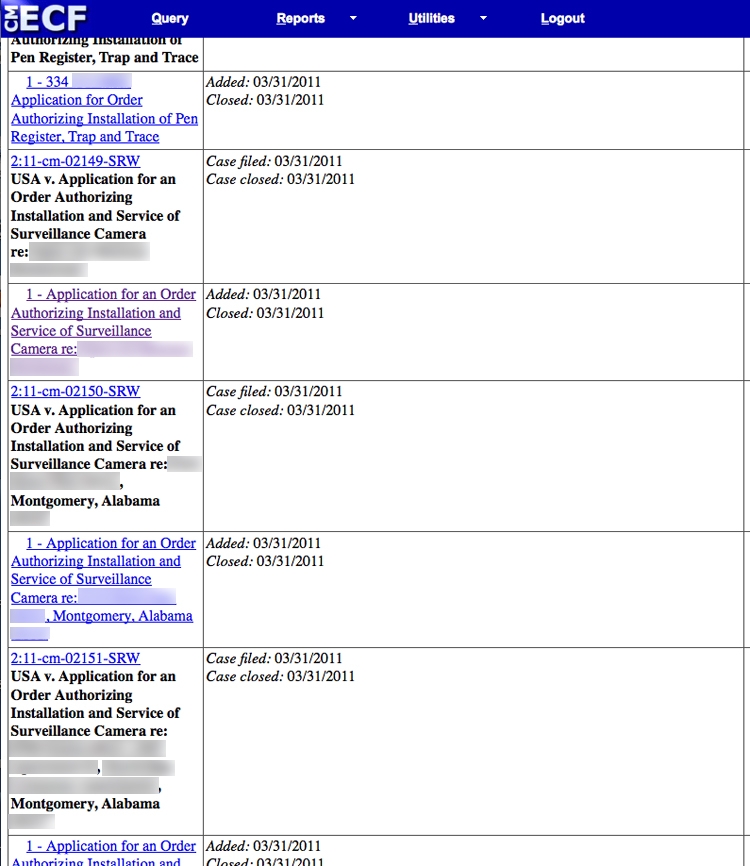
Additionally, on March 31, prosecutor Susan Redmond filed separate applications for court orders authorizing the “Installation and Service of Surveillance Camera” at two residences and one business in Montgomery. The applications were approved by Judge Susan Russ Walker, who signed an order sealing documents related to the surveillances.
 However, the corresponding PACER entries included the name of the business (which a reporter easily located) and the exact addresses of the two homes now being surveilled by federal agents. Click here to see a since-deleted PACER index page for the three applications, and here for a page containing additional details on one of the applications.
However, the corresponding PACER entries included the name of the business (which a reporter easily located) and the exact addresses of the two homes now being surveilled by federal agents. Click here to see a since-deleted PACER index page for the three applications, and here for a page containing additional details on one of the applications.
TSG will not further identify where the hidden cameras have been installed, since such a disclosure could compromise the government’s ongoing criminal investigation (though here, here, and here are photos of the targeted locations--blurred, of course, to render them unidentifiable).
Each of the 40 applications prepared by federal prosecutors would have had a notation on its face page that the document was filed “UNDER SEAL,” as seen in this excerpt from a prosecution request for AT&T telephone records.
Perhaps in the future those two words need to be rendered in larger type. And maybe even neon. (3 pages)







Comments (12)